jCSRF: automatic CSRF protection for Web 2.0 applications
Introduction
Cross-Site Request Forgery (CSRF, sometimes also XSRF) is a web
vulnerability that allows an attacker to submit requests to a web
application using a victim's user credentials. A successful attack can
lead to compromised accounts, stolen bank funds or information
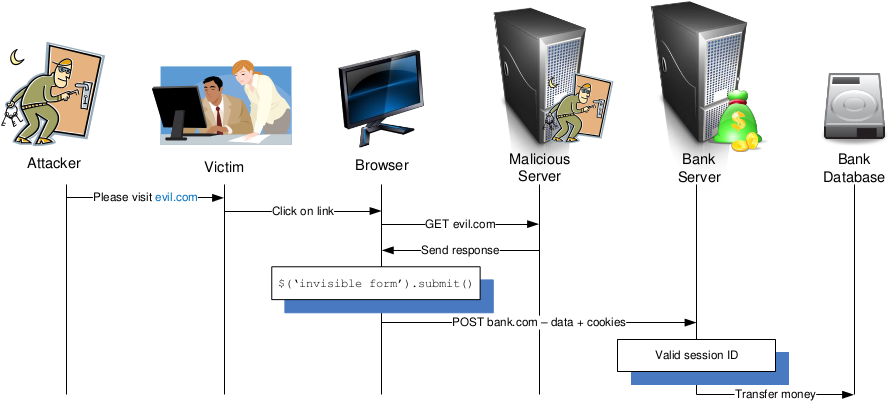
leaks. The figure below depicts a sample interaction required to
perform a CSRF attack: the user is lured on to a malicious site which
instructs the browser to send a form with values provided by the
attacker. Since the browser attaches the user's credentials to each
outgoing request regardless of its cause, the attacker in practice
uses the user's account to perform the actions specified by the form
data.
Description
To protect against CSRF attacks, we developed jCSRF, a dynamic server-side CSRF defense for Web Applications. Specifically, jCSRF has the following characteristics:
- No need for programmer effort or server-side modifications. jCSRF is enforced by a transparent proxy which does not need to assume anything about the web application being protected. This ensure that jCSRF can be used by legacy applications and that all languages (including binary applications) and frameworks are supported.
- Compatible with existing browsers. jCSRF only uses standard JavaScript features that are supported by all major browsers. Therefore, jCSRF can protect all website users.
- Protects dynamically generated requests. jCSRF also authenticates XMLHttpRequests and forms that are dynamically built using JavaScript. Static server-side defenses only authenticate forms that are provided directly in the HTML response. Thus, jCSRF is more compatible with recent web applications.
- Allows Cross-Origin Requests. Most solutions outright deny cross-origin requests, because it is the simplest policy against CSRF attacks, which require cross-origin requests. However, many applications require support for legitimate cross-origin requests and are broken by such a policy. jCSRF includes a protocol that constructs and embeds an unforgeable origin certificate in cross-origin requests, so that the target website can choose whether to allow the request.

Status
We have published a reference implementation along with the ACSAC paper. It is implemented in Python and implements all the features described in the paper. However, this is only a prototype that should not be used in production environments. Several features were never implemented, most notably support for IE, automatic packet routing for Windows hosts and support for HTTP 1.1.Download
The reference implementation is available under the GPL here. Installation instructions can be found in the included README file.
Acknowledgements
This work was supported in part by an an ONR grant N000140710928, an NSF grant CNS-0831298, and an AFOSR grant FA9550-09-1-0539.



